Understanding the Risk Management Process - Part 1

In this series of articles, I will discuss the Risk Management process, its elements and challenges.
The first fundamental element of successful cybersecurity architecture is the risk management process. The risk management process can act as a starting point and can be adapted to specific enterprise needs.
The risk management process involves a systematic analysis to determine where an enterprise may have compromises, the consequences of those compromises, and ways to reduce the probability or severity of those consequences. The risk management process is represented below and can be adapted for specific enterprise needs.
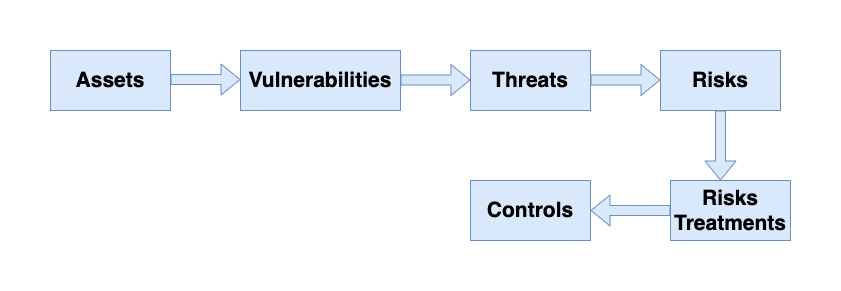
Assets
Risk management starts with “assets,” which are things the enterprise wants to protect. Generally, there are four types of assets of interest:
- Personnel: the people in the organization and their knowledge and abilities.
- Facilities: the locations where people work and the tools and equipment at those locations.
- Processes: the procedures whereby the organization operates and the systems it uses to accomplish its goals.
- Information: the data held by the enterprise, whether it is proprietary, customer, or business data.
All these assets must be protected.
Vulnerabilities
The next risk management step considers “vulnerabilities,” which are ways the assets can be compromised. For example, a facility vulnerability may be where one side of the facility is adjacent to an abandoned building. A vulnerability for a business process may be that it relies on an IT system that is extremely unreliable. IT systems vulnerabilities can be further characterized in terms of the “CIA” of cybersecurity:
- Confidentiality, meaning protecting the secrecy of data
- Integrity, meaning protecting data from unauthorized changes
- Availability, meaning the availability of IT systems and the data the systems host to those who need the data when it is needed.
Threats
The next risk management step considers “threats,” which are ways in which vulnerabilities can be exploited to cause damage to the asset. Threats may be natural or man-made, accidental or deliberate, random or deterministic.
Considering threats is one of the most creative steps in the risk management process. Considering threats involves a lot of “Murphy’s Law” thinking (What can possibly go wrong?) and thinking like attackers (What vulnerabilities can be exploited?). It is helpful to think about threats in terms of how they would affect the confidentiality, integrity, and availability (in other words, CIA) of the enterprise’s information and information systems.
Risks
The next risk management step identifies and evaluates risks. Combining threats with vulnerabilities, risks can be identified. A threat against a well-protected area generally produces a low level of risk, while a threat against an area where the enterprise is not well protected produces a risk that must be considered.
Unfortunately, identifying and evaluating risks is fundamentally a judgment call. There are two challenges here:
- Underestimating risk because vulnerability is underestimated.
- Missing a risk because a particular threat scenario is not considered.
Risk Treatment
Once risks have been evaluated, the next step is to address “risk treatment.” There are a number of ways to handle risk, besides just trying to prevent the bad thing from happening.
- The first way to handle risk is to “avoid” the risk by eliminating the vulnerability or the threat.
- The second way to handle the risk is to “mitigate” the risk by reducing the probability that it will occur or the impact when it does occur.
- The third way to handle the risk is to “share” the risk by introducing a third party—such as an insurance company—that will compensate the enterprise in the event that the risk occurs.
- The fourth way to handle the risk is to “retain” the risk, where the enterprise simply accepts the possibility that the risk may occur and deals with the consequences when they happen; self-insurance is a good example of this approach.
Controls
The next risk management step, especially if the enterprise chooses to reduce the risk, is to apply security “controls.” Security controls can do four things.
- First, controls can reduce the probability the risk will occur or make it more difficult for attackers to execute on the risk.
- Second, controls can reduce the impact when the risk does occur, perhaps limiting the amount of damage that occurs.
- Third, controls can detect the occurrence of the risk happening, allowing for active responses to contain the damage and reduce the potential exposure.
- Fourth, controls can collect evidence that is used to show the operation of security controls, to detect failures of the controls, or to support investigations after an incident has occurred.
Next, I'll discuss risk analysis and mitigation, stay tuned 😊
